Windows Discovery Troubleshooting
1. Windows Server 2008R2 - TLS issue ansible connection
Issue:
Win_ping to windows 2008 R2 host machine
Ansible version:-
ansible 2.9.4
config file = /etc/ansible/ansible.cfg configured module search path = ['/root/.ansible/plugins/modules', '/usr/share/ansible/plugins/modules'] ansible python module location = /usr/local/lib/python3.6/site-packages/ansible executable location = /usr/local/bin/ansible python version = 3.6.8 (default, Oct 11 2019, 15:04:54) [GCC 8.3.1 20190507 (Red Hat 8.3.1-4)]
Result:
192.152.1.21 | UNREACHABLE! => {
"changed": false,
"msg": "basic: HTTPSConnectionPool(host='192.152.1.21', port=5986): Max retries exceeded with url: /wsman (Caused by SSLError(SSLError(1, '[SSL: UNSUPPORTED_PROTOCOL] unsupported protocol (_ssl.c:897)'),))",
"unreachable": true
}
Expected Result:
192.152.1.21 | SUCCESS => {
"changed": false,
"ping": "pong"
}
Points to Note: 1. This has nothing to do with certificate validation. 2. If it had been, you would have gotten a completely separate error message saying something like "certificate verify error" or something similar. 3. This is an error that Python/OpenSSL reports when it cannot negotiate a common TLS protocol between the itself and the Windows server. 4. You can run the following to try and get some more info
ANSIBLE_PYTHON=$(head -1 $(which ansible) | cut -c 3-)
echo $ANSIBLE_PYTHON # Used to just display what Python Ansible is using
$ANSIBLE_PYTHON --version
Make sure both match, if they don't then the openssl binary is at a different path and these tests won't indicate anything
$ANSIBLE_PYTHON -c "import ssl; print(ssl.OPENSSL_VERSION)"
openssl version
openssl s_client -connect hostname:5986
Prints a list of ciphers and the protocols that the openssl supports, once again the binary should be the one Python is compiled against.
openssl ciphers -s -v
-
In this example is a snippet of what was received from the s_client -connect command
--- SSL handshake has read 2105 bytes and written 465 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384 Server public key is 4096 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES256-GCM-SHA384 Session-ID: DA300000338CE777889199F6BFBB5D2D0922405E01E413959C82ABF8B5433E0D Session-ID-ctx: Master-Key: 62132D2AB686ABA5CEAB04DD0E92AD51140F658693E8643421207CDE599FF6588B00C2EC84E410F17E077856204735A8 Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None Start Time: 1580898057 Timeout : 300 (sec) Verify return code: 21 (unable to verify the first certificate) ---You can see that the protocol negotiated between the client and the server was TLSv1.2, which is good. In this case we would expect the handshake to fail because it cannot negotiate a common protocol. Once again you need to make sure the openssl binary you run is the one that your Python has been compiled against.
-
Typically when a common protocol is not found it means one of the following;
- Python's OpenSSL does not support TLS 1.2 and the Windows host only offers TLS 1.2
- Typical for older hosts talking to newer Windows versions
- MacOS before High Sierra used an ansible OpenSSL version which did not support TLS but based on your controller OS version I doubt this is the case for you
- Python's OpenSSL only supports TLS 1.2 or newer and the Windows host does not offer TLS 1.2
- Some newer distros disable older TLS protocol for security reasons
- TLS 1.2 has been enabled by default for Server 2012/Windows 8 or newer
- Server 2008 R2/Windows 7 need a security update to be applied and some registry settings tweaked
- https://www.nartac.com/Products/IISCrypto/Download is a great tool you can use to control the TLS protocol and ciphers offerred by a Windows server if you don't want to edit the registry
- Python's OpenSSL does not support TLS 1.2 and the Windows host only offers TLS 1.2
-
A final thing you can do is setup a Wireshark capture between the Ansible controller and Windows host, most of the data is going to be garbage due to the encryption but you can see the negotiation process happen in plain text. For example the controller will send a Client Hello message which advertises the protocols and cipher suites it can use
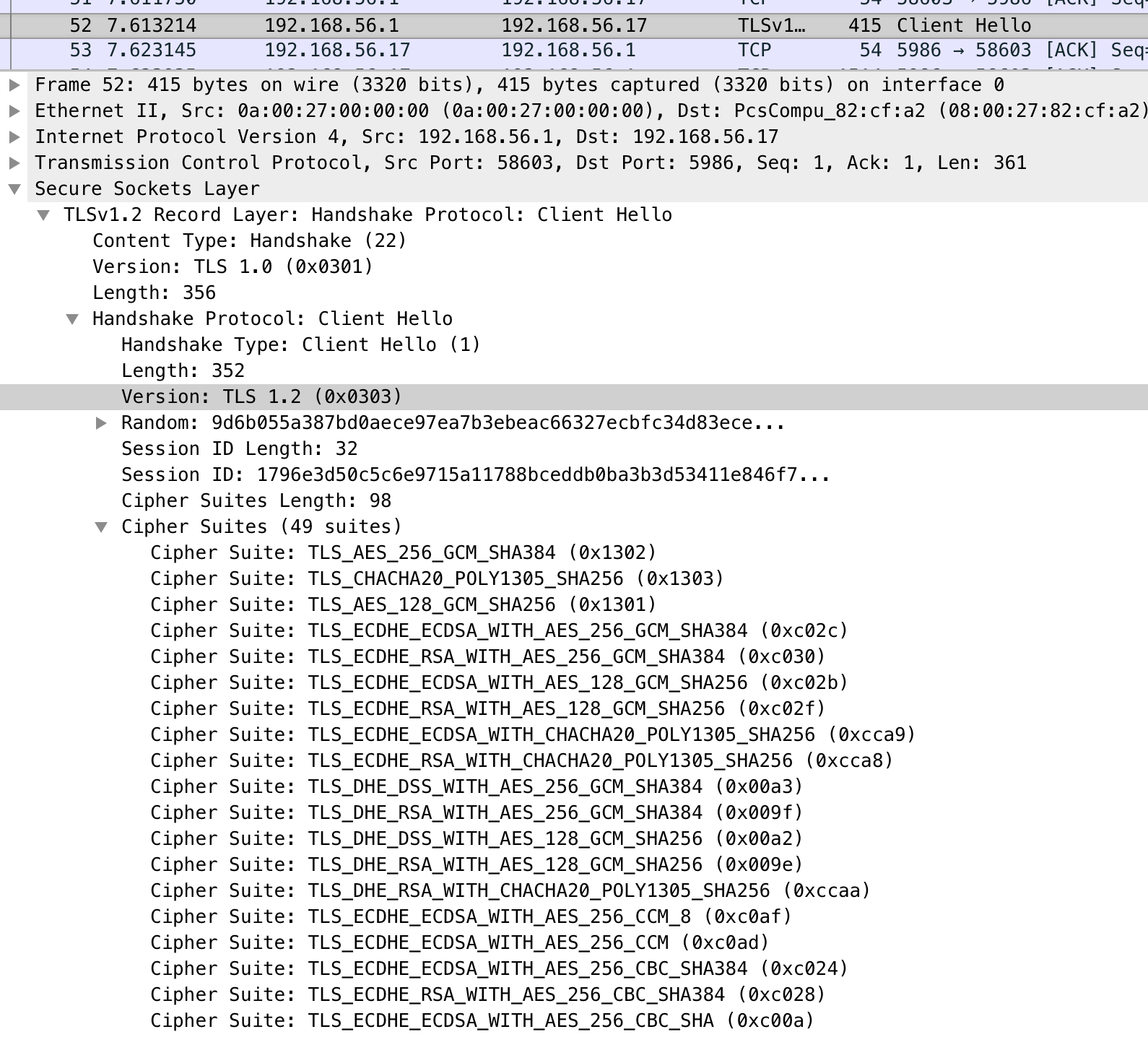
The Server Hello response tells you what protocol and cipher suite was ultimately chosen
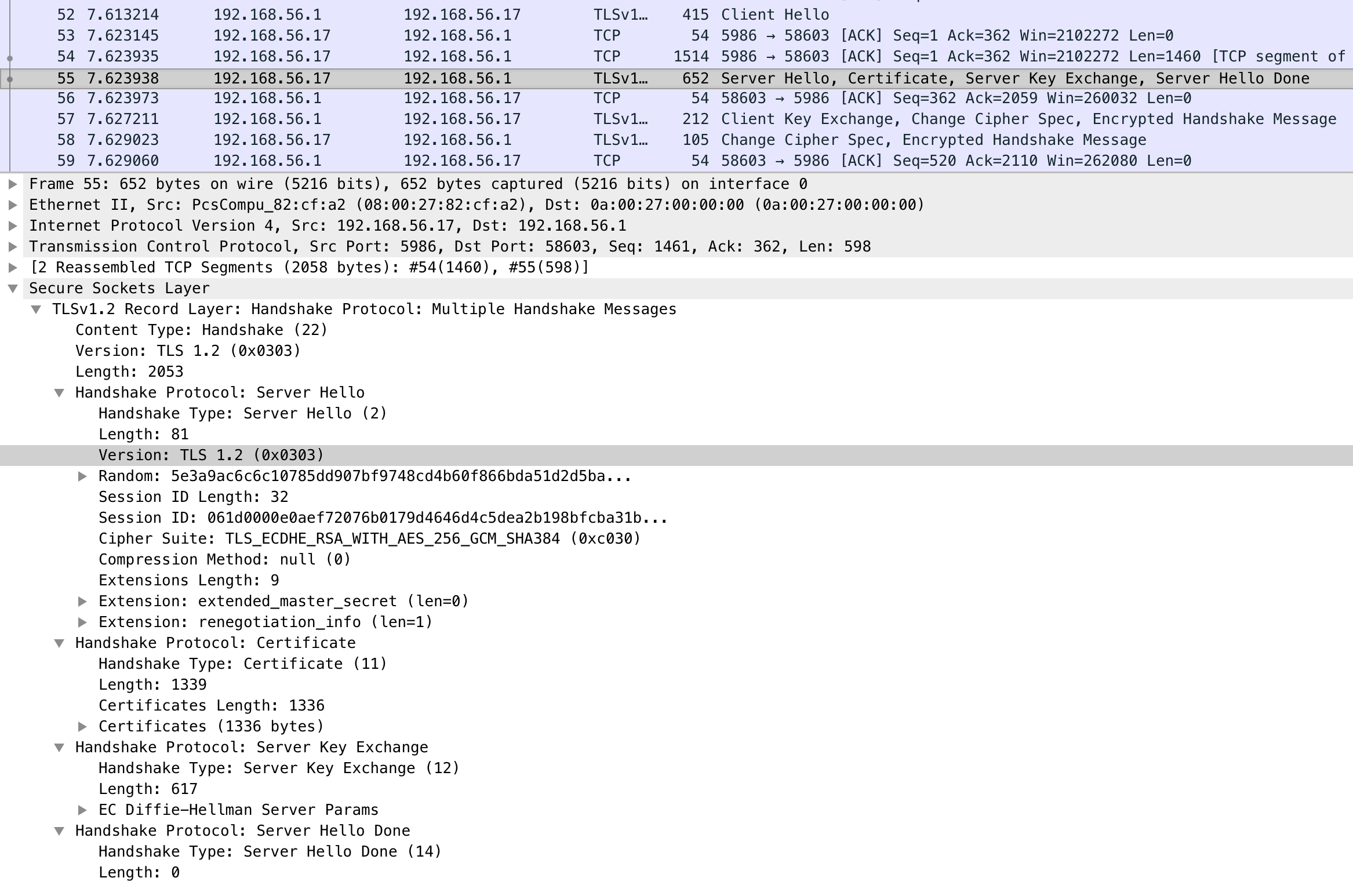
Lastly I believe the Windows application or system event log shows errors when a client tries to access the server but the server does not have a common protocol, that's another good place to look.
Solution:
Try running below powershell script and check ansible win_ping. This will result expected output. enableTLS.ps1 link